How to Set up Azure Active Directory to perform authentication using Single Sign-On
This section explains on how to perform Single Sign-On for users in Azure Active Directory with Syncfusion Report Server and Report Designer.
NOTE
This configuration has been done using the Azure Portal
Steps to set up Azure Active Directory
Prerequisites
- An Azure account with Active Directory support
- Install Syncfusion Report Server and Login with Administrator account
Setup Azure Active Directory application
Log on to the Azure portal to create an Azure Active Directory.
-
Click
Create a resourceand searchAzure Active Directoryas follows.
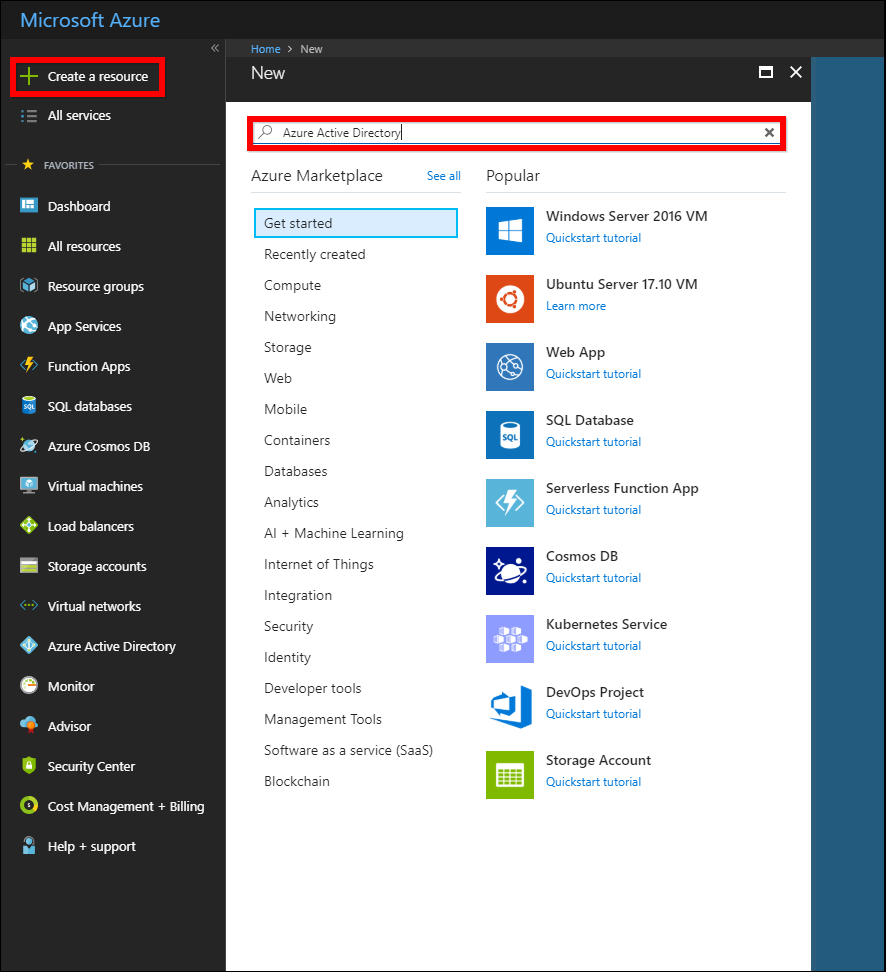
-
Click
Createin the following screenshot.
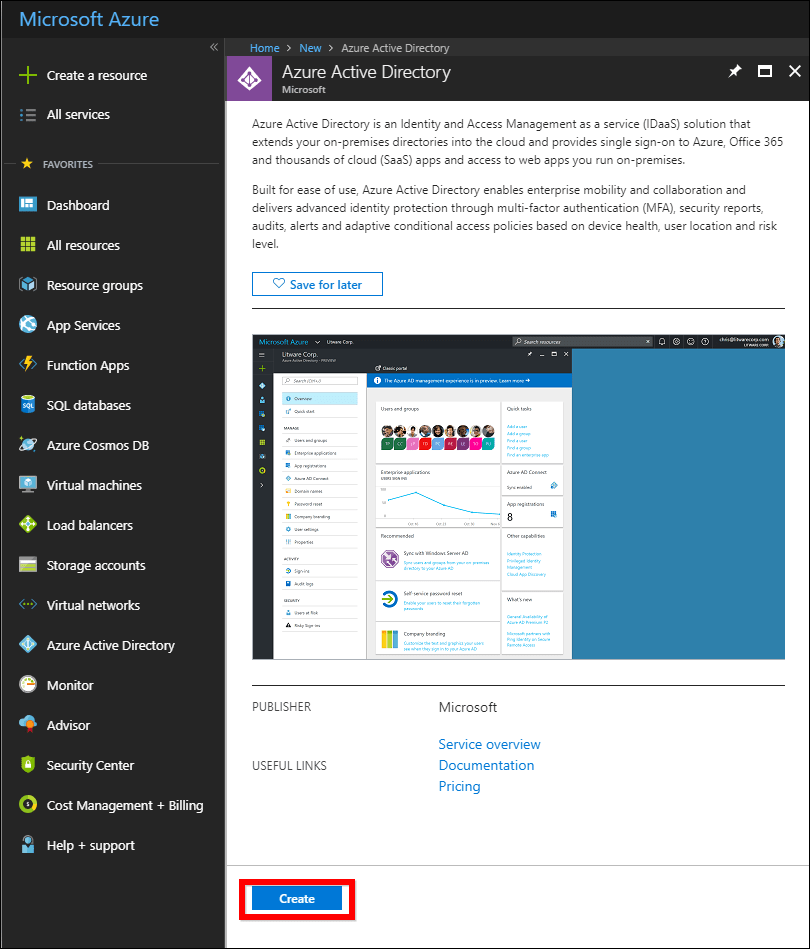
-
In the dialog box, enter the
Name,Domain Name, and choose theCountry or Region, and then clickCreate.
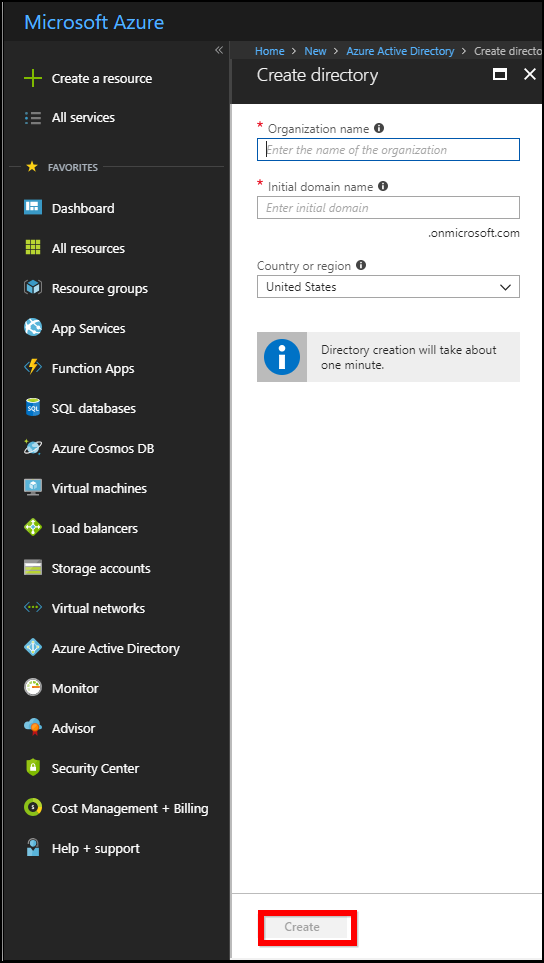
The application will be added to the directory and you can view the details of the application in the App registrations.
In this directory, you should add two applications. An application acts as a Web API Server (Report Server), and the other application act as native client application (Report Designer).
- Enter into the created directory and click
Azure Active Directory, and then selectApp registrations. -
Now, click
New application registrationto add a new application.
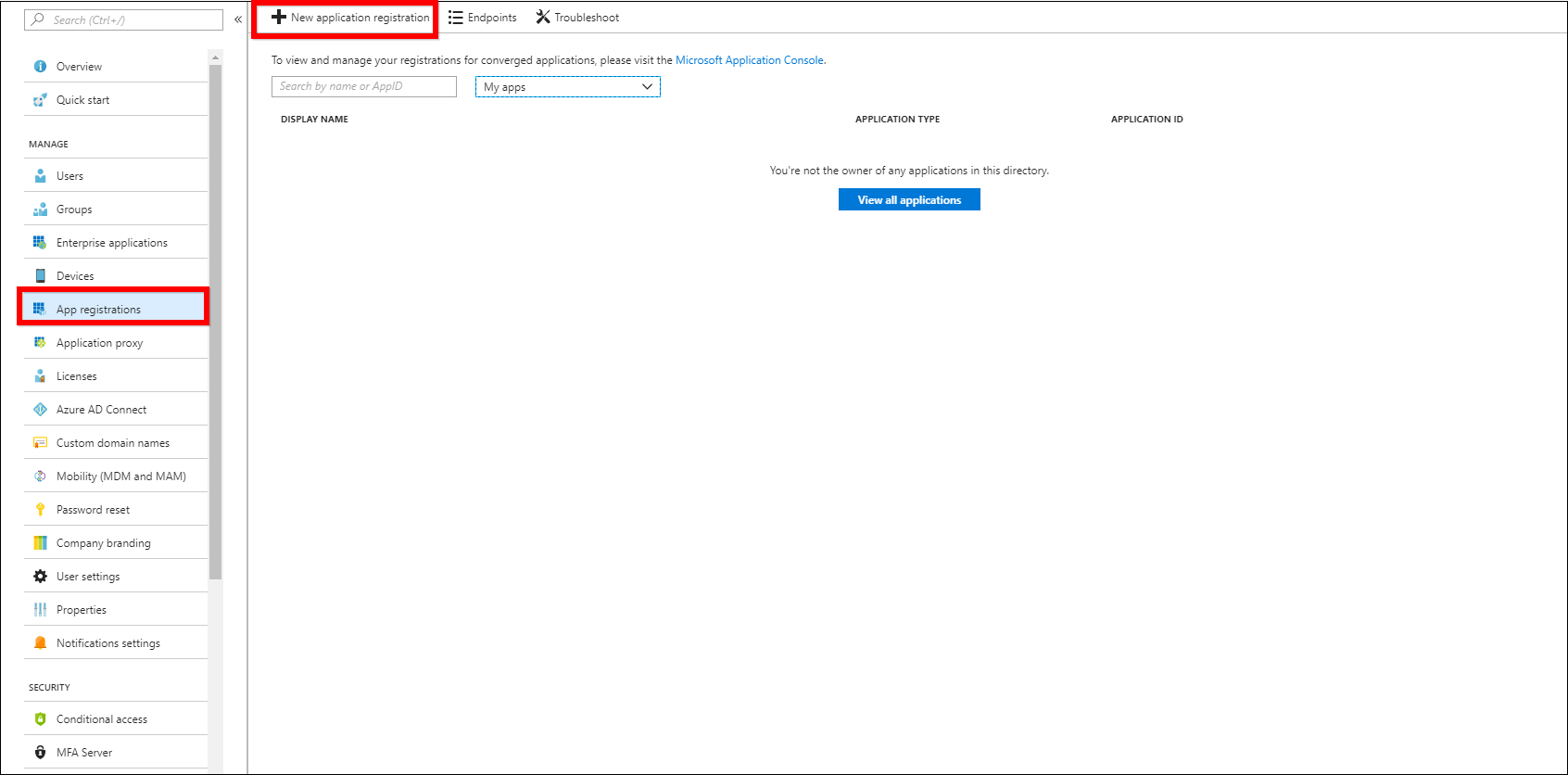
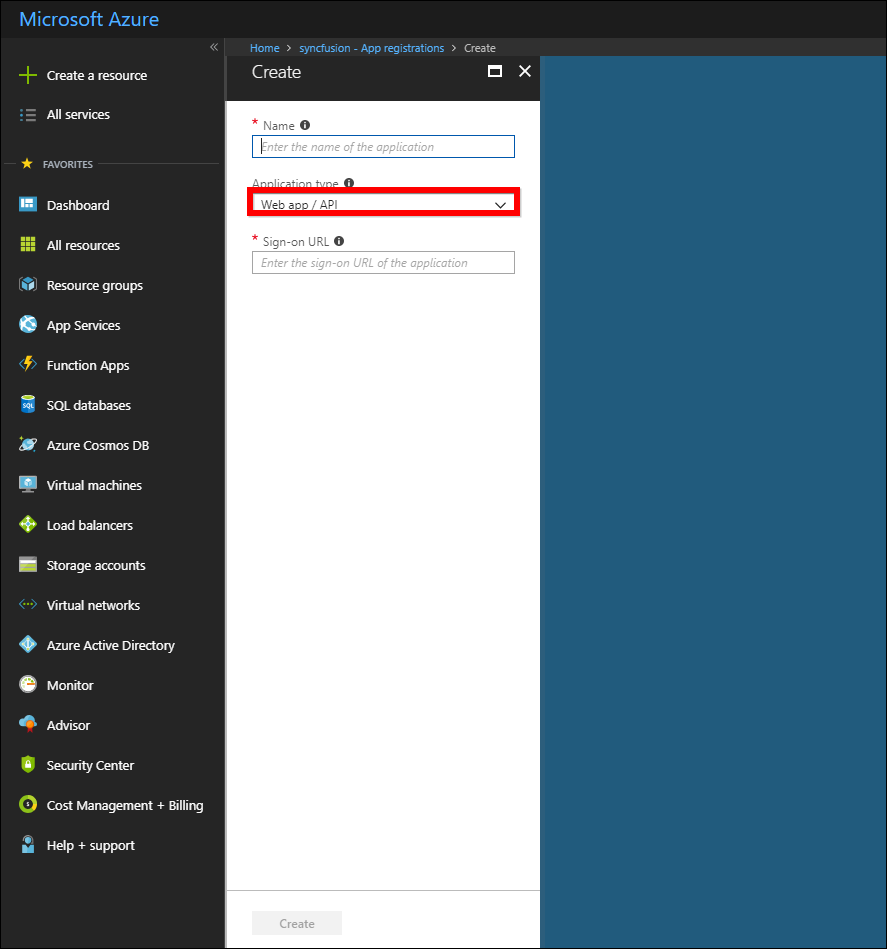
-
Enter the name of the application and choose
Web app/APIas Application type and enter the sign-on URL.
-
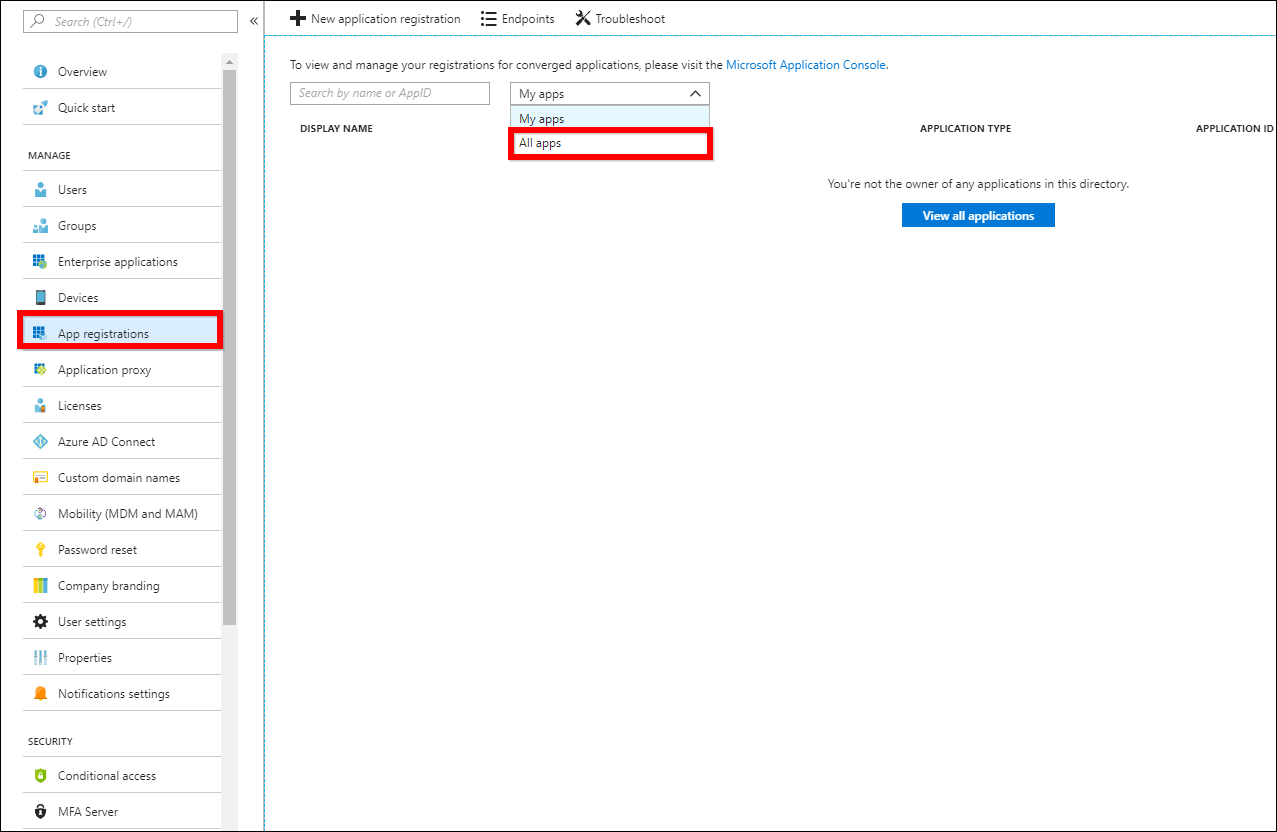
To view all registered applications, click
Azure Active Directoryand selectApp registrations, and then chooseAll apps.
-
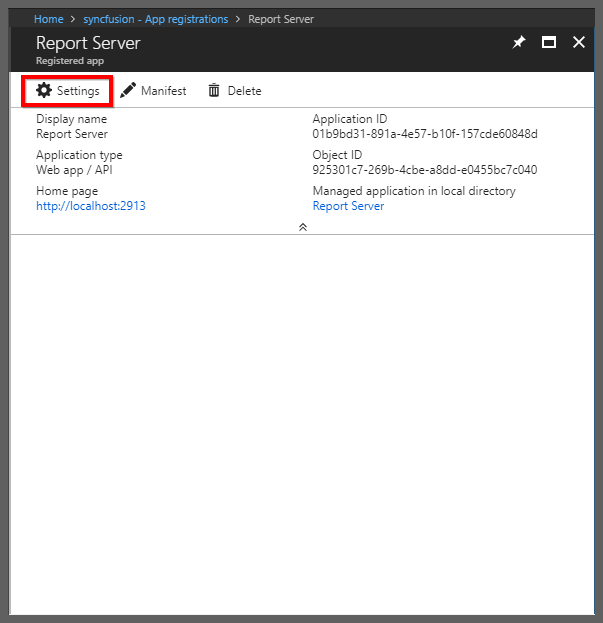
Choose the registered application and click
Settings.
-
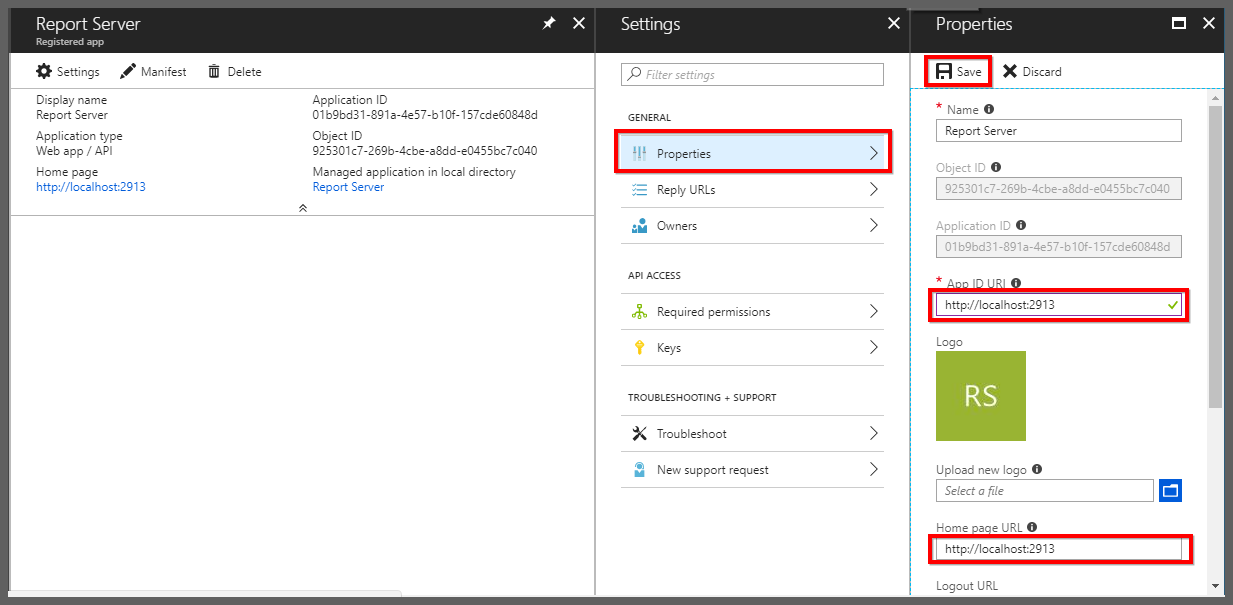
Select
Propertiesand enter theApp Id URIandHome page URL.
- Click
Saveas highlighted in the above screenshot.
NOTE
The sign-on URL, App ID URI, and Home page URL should be the URL of the Syncfusion Report Server application.
Now, you can add Microsoft Graph application to your application to import the users and groups into the Syncfusion Report Server.
-
Go to application, click
Settings, and select theRequired permissions. Then clickAddand clickSelect an API.
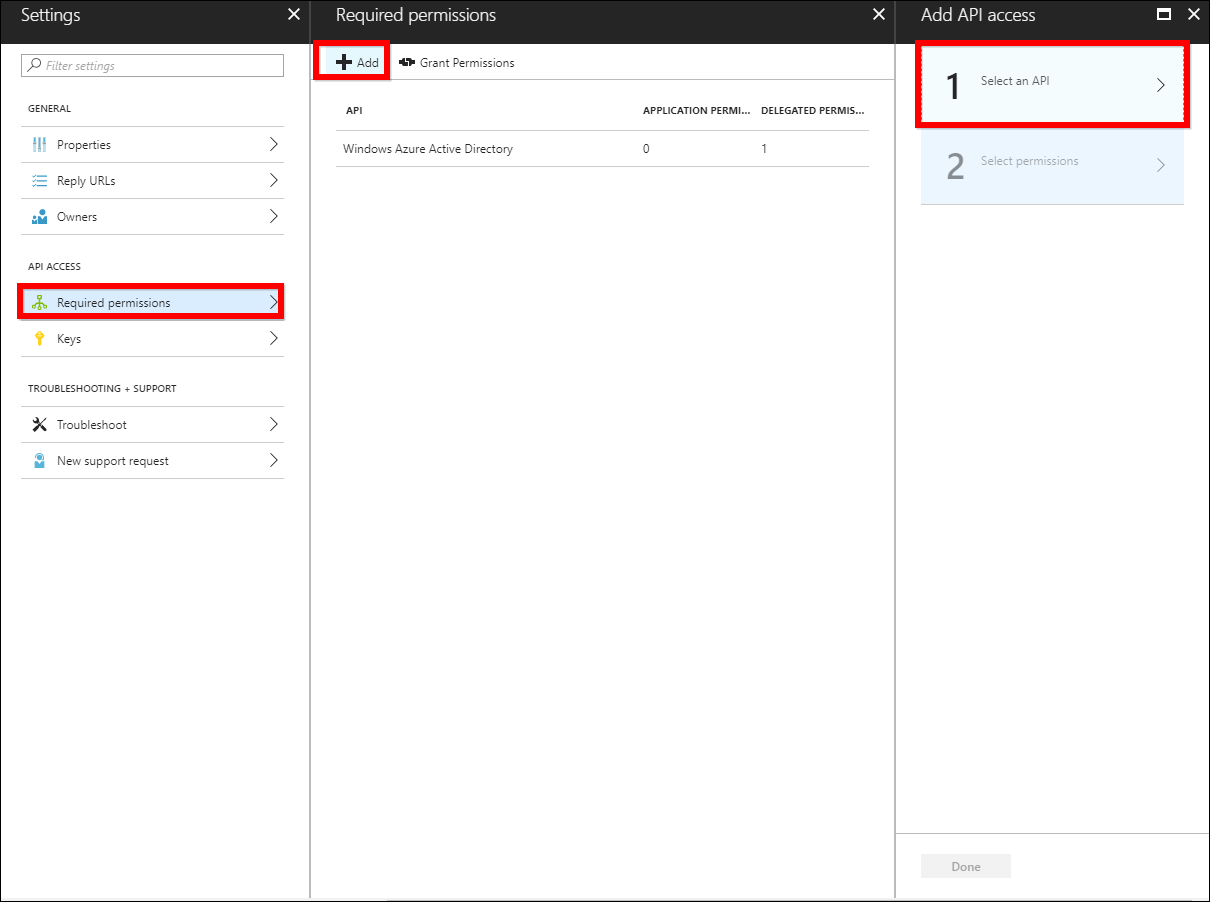
-
Select
Microsoft Graphfrom the list and clickSelect.
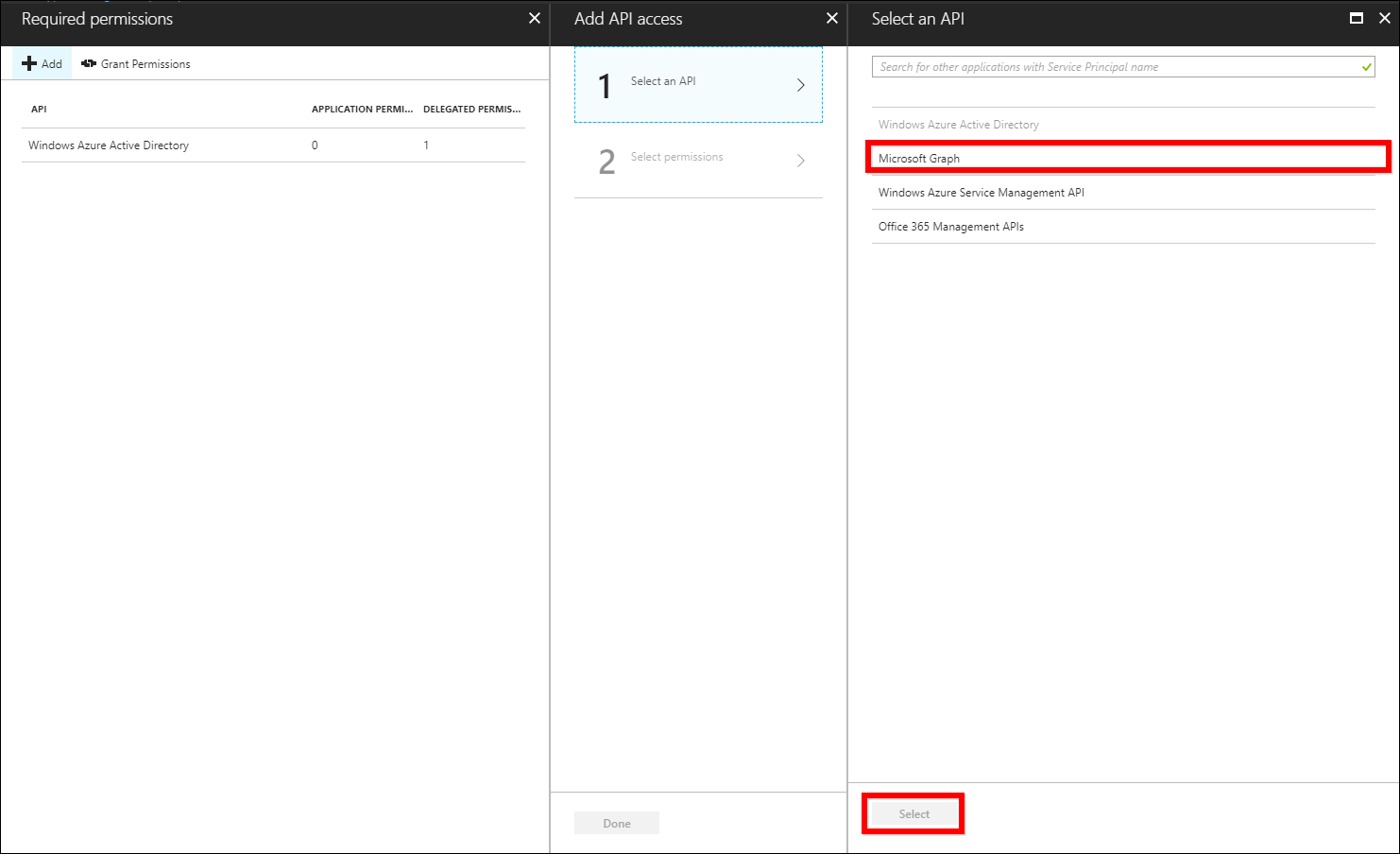
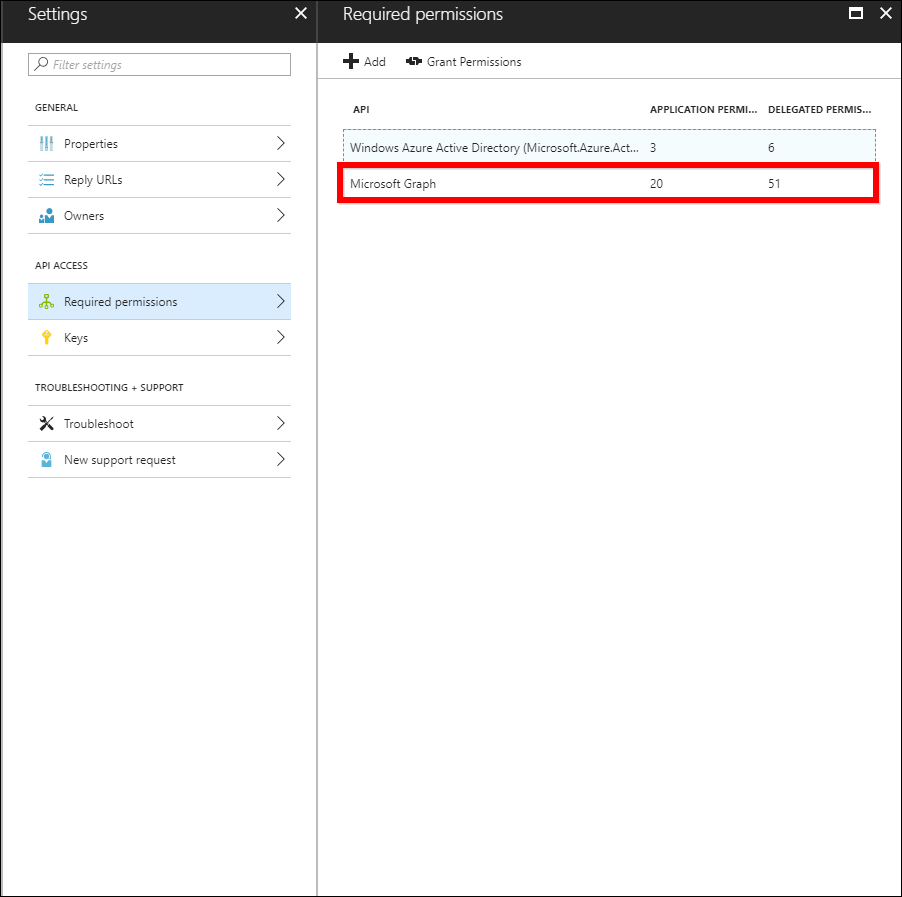
-
Enable following permissions for Report Server application
- Microsoft Graph Application and Delegated Permissions
Application Permissions Read directory data Delegated Permissions 1. Read directory data 2. Read all groups 3. Sign in and read user profile 4. Access directory as the signed in user - Windows Azure Active Directory Application and Delegated Permission
Application Permissions Read directory data Delegated Permissions 1. Read directory data 2. Sign in and read user profile -
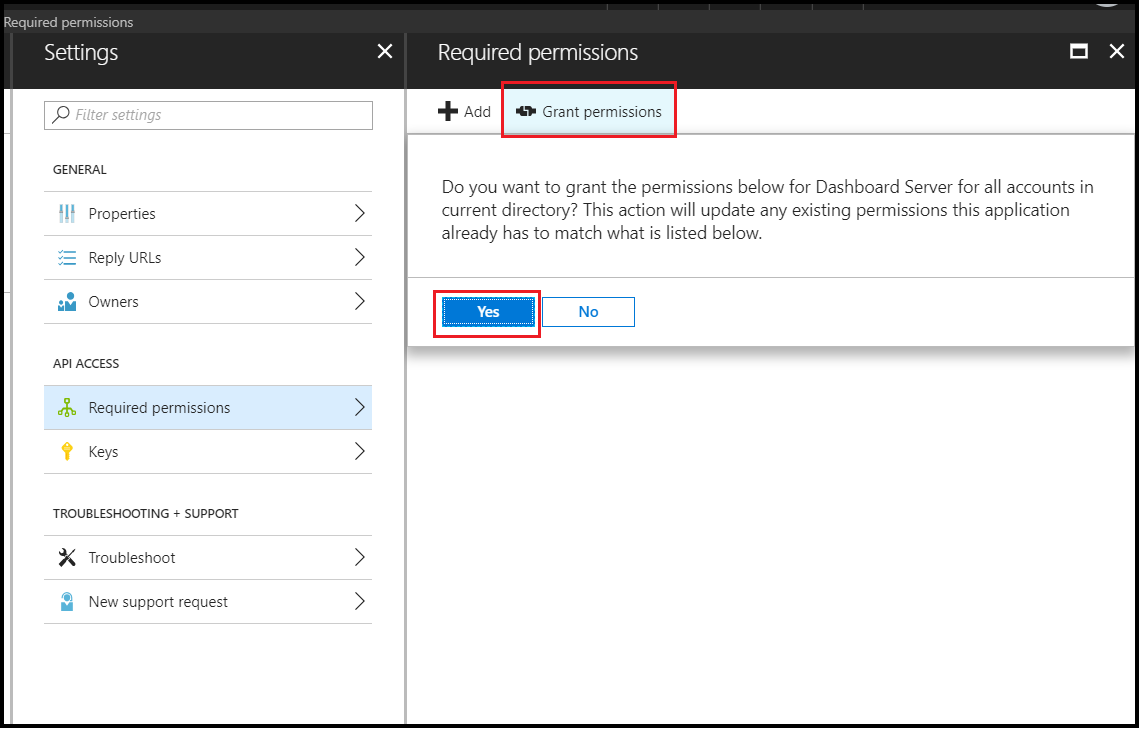
After adding the permission, click the
Grant Permissionfrom theRequired permissionssection of the application page and selectyesas below.
Configure Azure Active Directory to perform Single Sign-On in Report Designer application
-
Enter into the created directory and click the
Azure Active Directory. Then, selectApp registrationsand click theNew application registrationto add a new application.

-
Enter the name of the client application and choose the Application type as
Nativeand enter theRedirect URI.
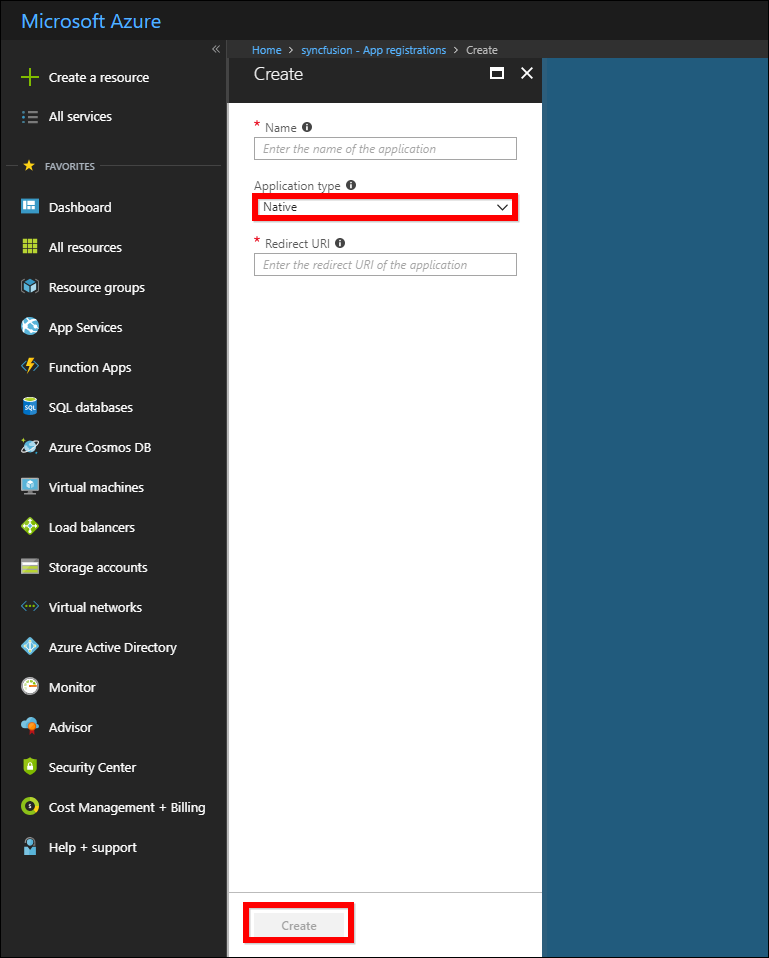
-
Click
Create. The client application will be added to the directory and you can view the details of the application in theApp registrations.
NOTE
Redirect URI should be the URL of the Syncfusion Report Server application.
-
To view all registered applications, click the
Azure Active Directoryand selectApp registrations, and then chooseAll apps.

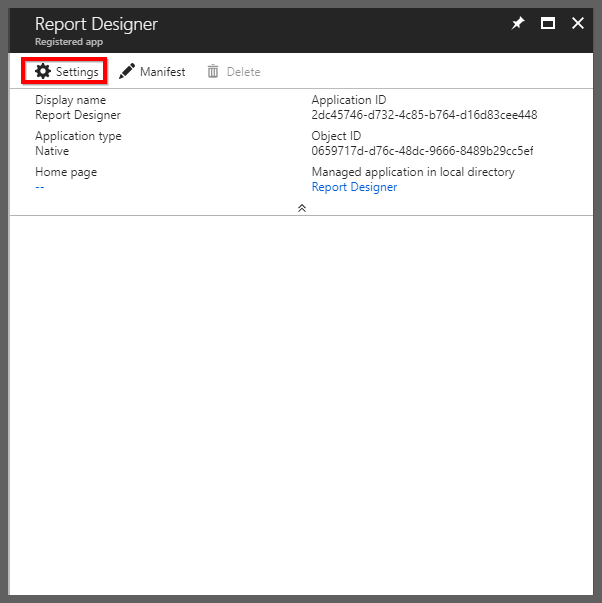
Now, you can add
Report Serverapplication to the client application to enable Single Sign-On in native client application. -
Choose the registered application and click the
Settings.
-
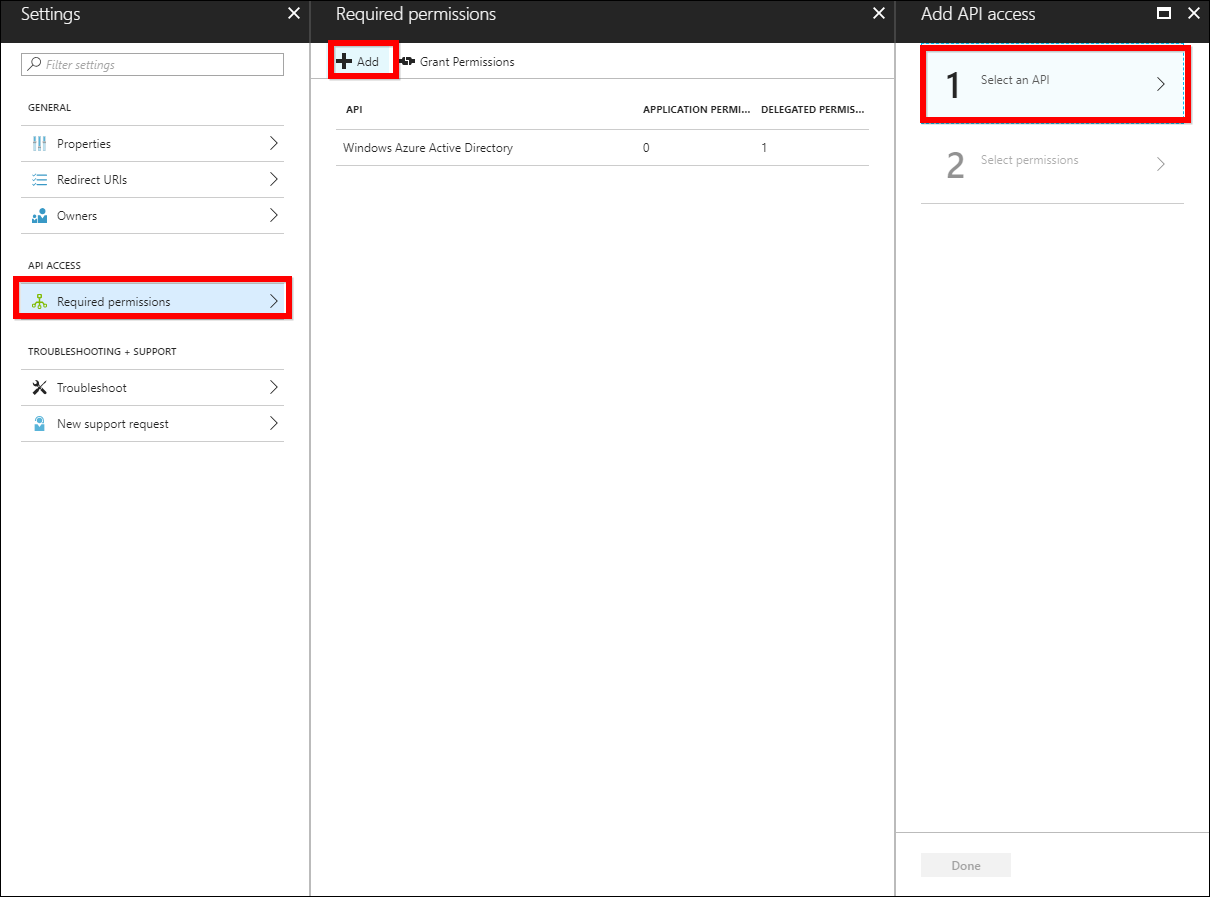
Go to application, click
Settings, and selectRequired permissions. Then clickAdd, and then chooseSelect an API.
-
Select the
Report Serverfrom the list and clickSelect.
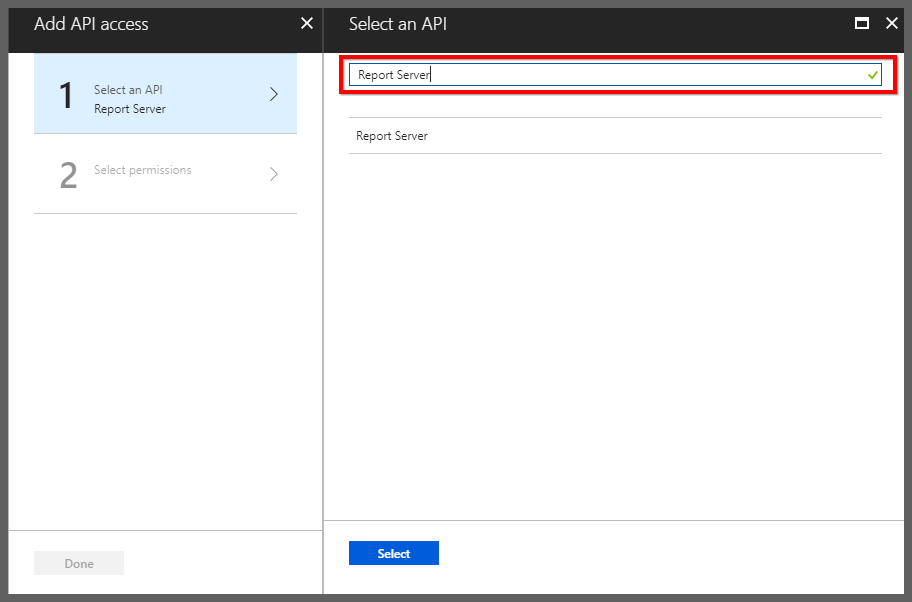
-
Select the delegated permission for accessing Report Server and save it.
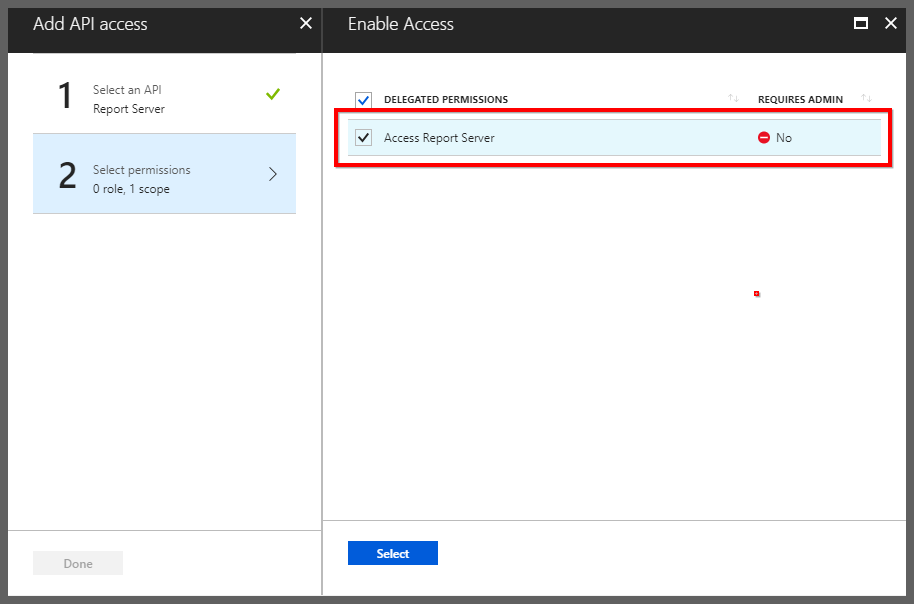
Setup Azure Active Directory users and groups
By default, a root user sourced from the Microsoft account is added to the directory. You can add users to this directory and later it will be imported to the Syncfusion Report Server to perform the Single Sign-On.
Setup Syncfusion Report Server to perform Single Sign-On
Configure the settings in Syncfusion Report Server to perform Single Sign-On.
-
When you are in the same Azure Active Directory application (Report Server) page, go to
App registrations, and clickEndpointsat the top, and a pop-up will be appeared as follows.
-
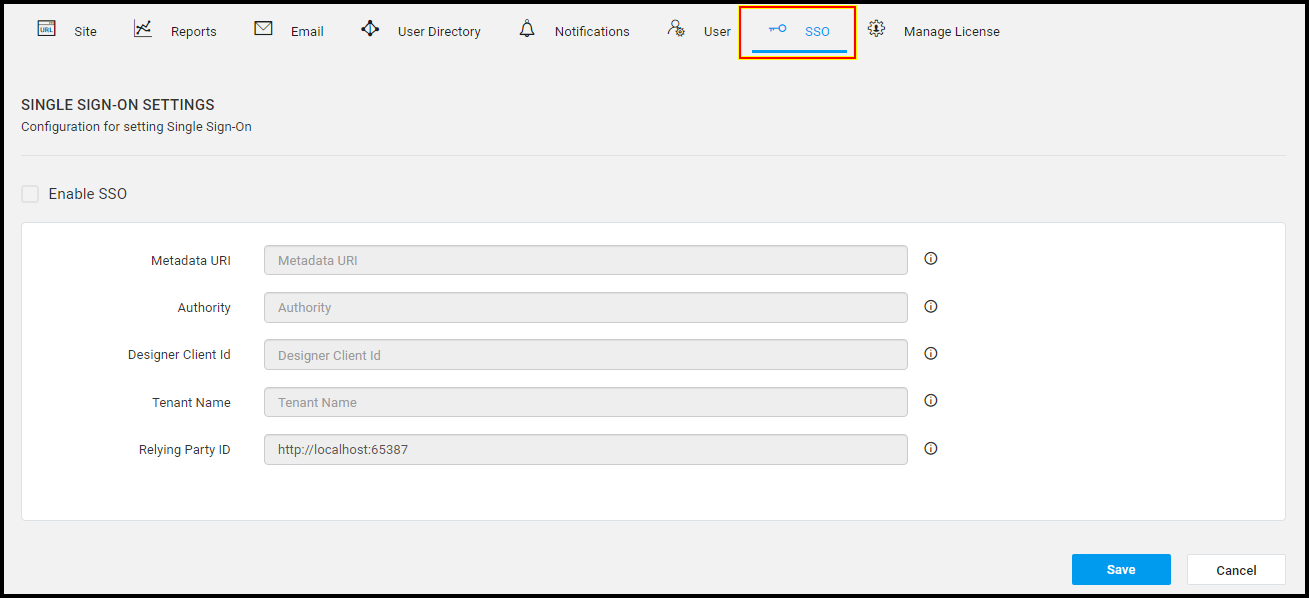
Start Syncfusion Report Server and log on with administrator account. Click the
Settingsicon in the bottom-left corner and select theSSO settings.
-
Configure the following fields in the Syncfusion Report Server to perform Single Sign-On with Report Server.
-
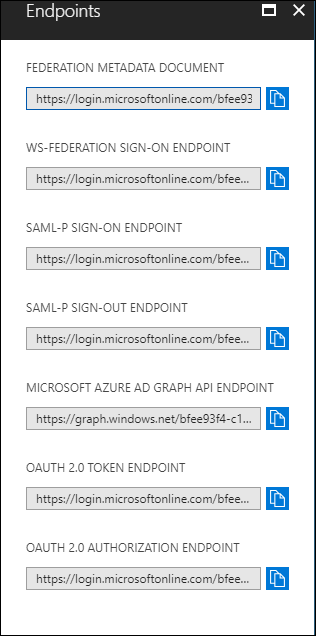
Metadata URI: Copy the text in the first textbox named
FEDERATION METADATA DOCUMENTand paste it. -
Relying Party ID: The default site URL is already defined in this field. Copy this URL and go to configure menu of the server application created in the Azure. Paste the URL in
Sign-on URL,App ID URI, andReply URLand save the application.
-
-
Configure the following fields in the Syncfusion Report Server to perform Single Sign-On with Report Designer.
-
Authority: From the Azure application, click the view endpoints. A pop-up will be displayed. Copy the text in the second textbox named
WS-Federation Sign-On Endpointand paste it. -
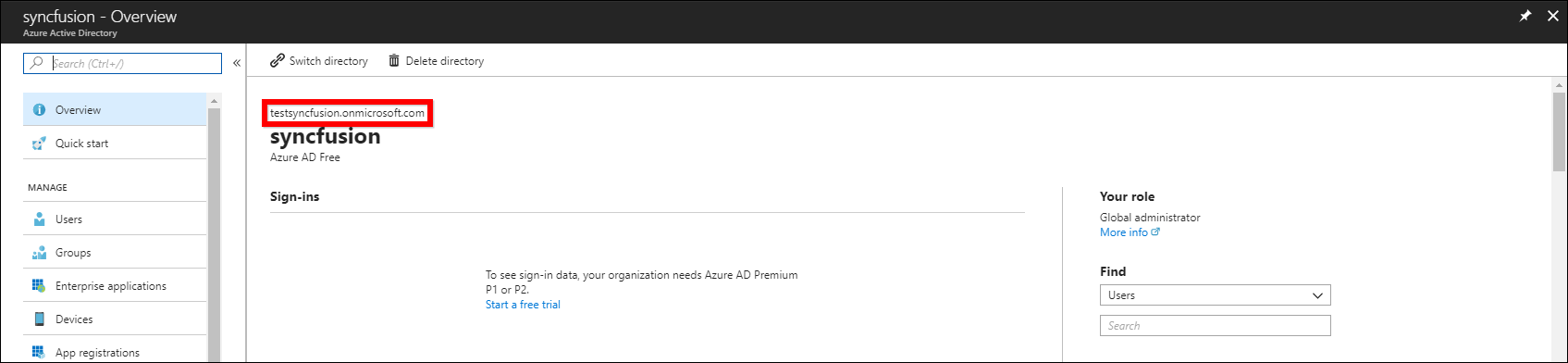
Tenant Name: Go to the created
Azure Active Directoryand copy the domain name by clicking it as shown in the following image.
-
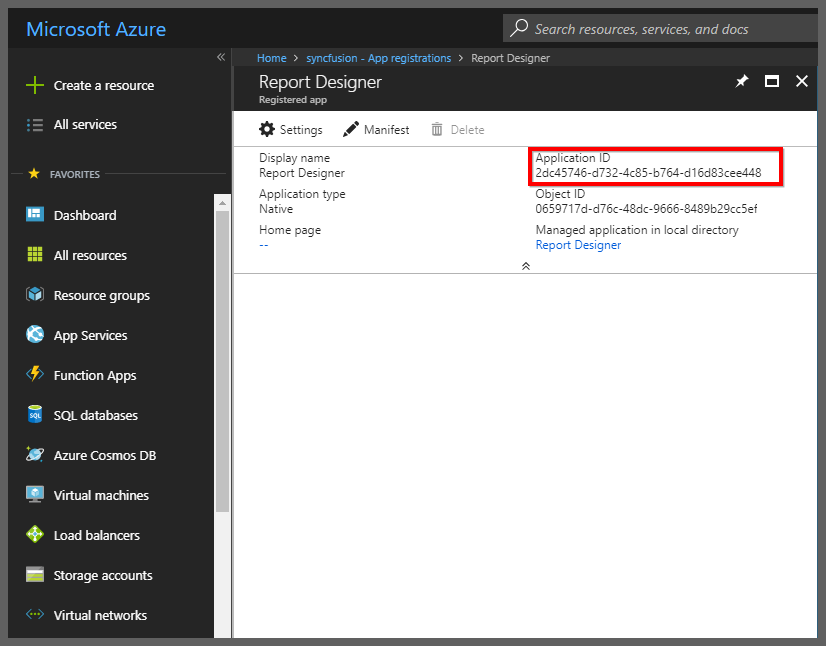
Designer client ID: Go to the registered application and click the
Settings. Then, copy theApplication Idand paste it.
-
-
Now, click save. After the values are saved, the application is
Restartedto apply the settings.
Setup Syncfusion Report Server to import Azure Active Directory users and groups
-
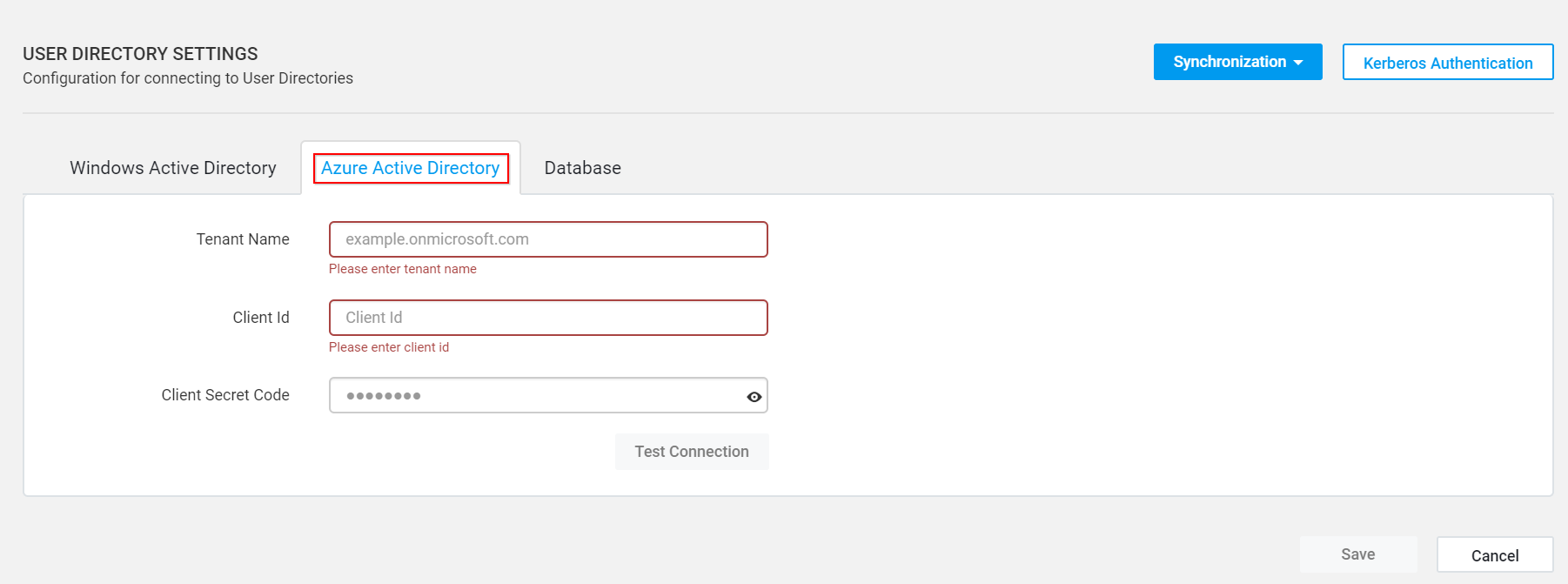
Go to the
Active Directory Settingspage in the Syncfusion Report Server and click theAzure Active Directorytab.
-
Configure the following fields in the Syncfusion Report Server to import Azure users and groups.
-
Tenant Name: Go to the created
Azure Active Directoryand copy the domain name by clicking it as follows.

-
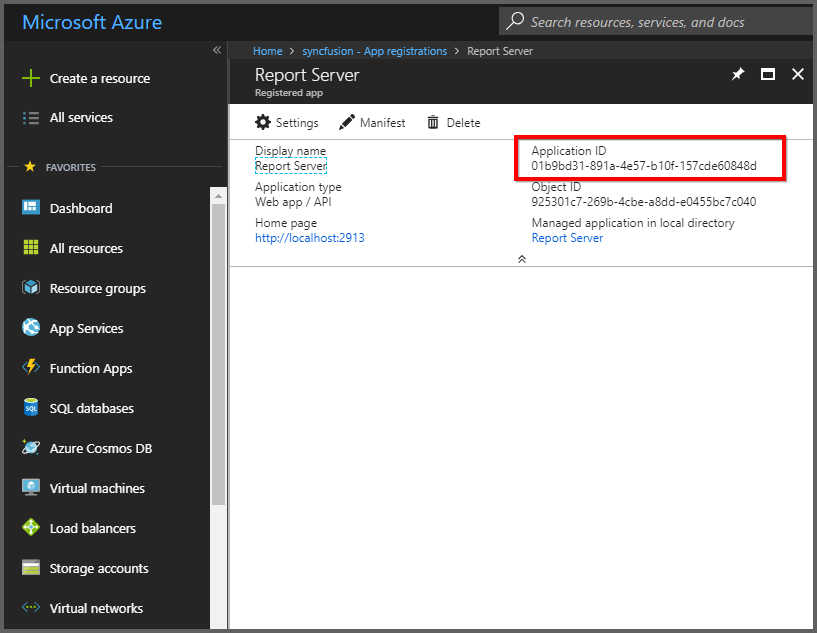
Client ID: Go to the registered application and click the
Settings, and then copy theApplication Idand paste it.
-
Client secret code: Go to the
Settingsand clickKeys, and then enter theDescriptionand choose theDurationunderPasswords.
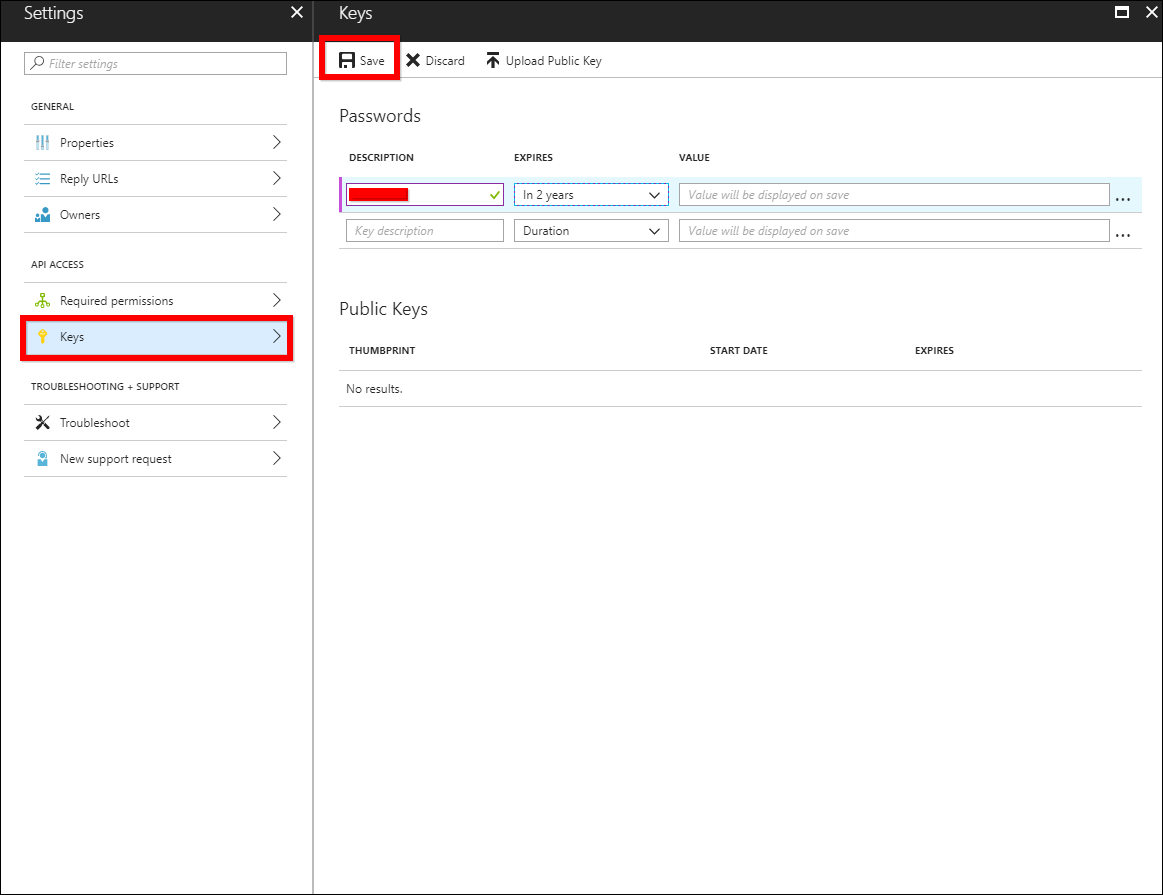
-
-
Click
Save. Theclient secretwill be generated, and then copy and paste it into the text box.
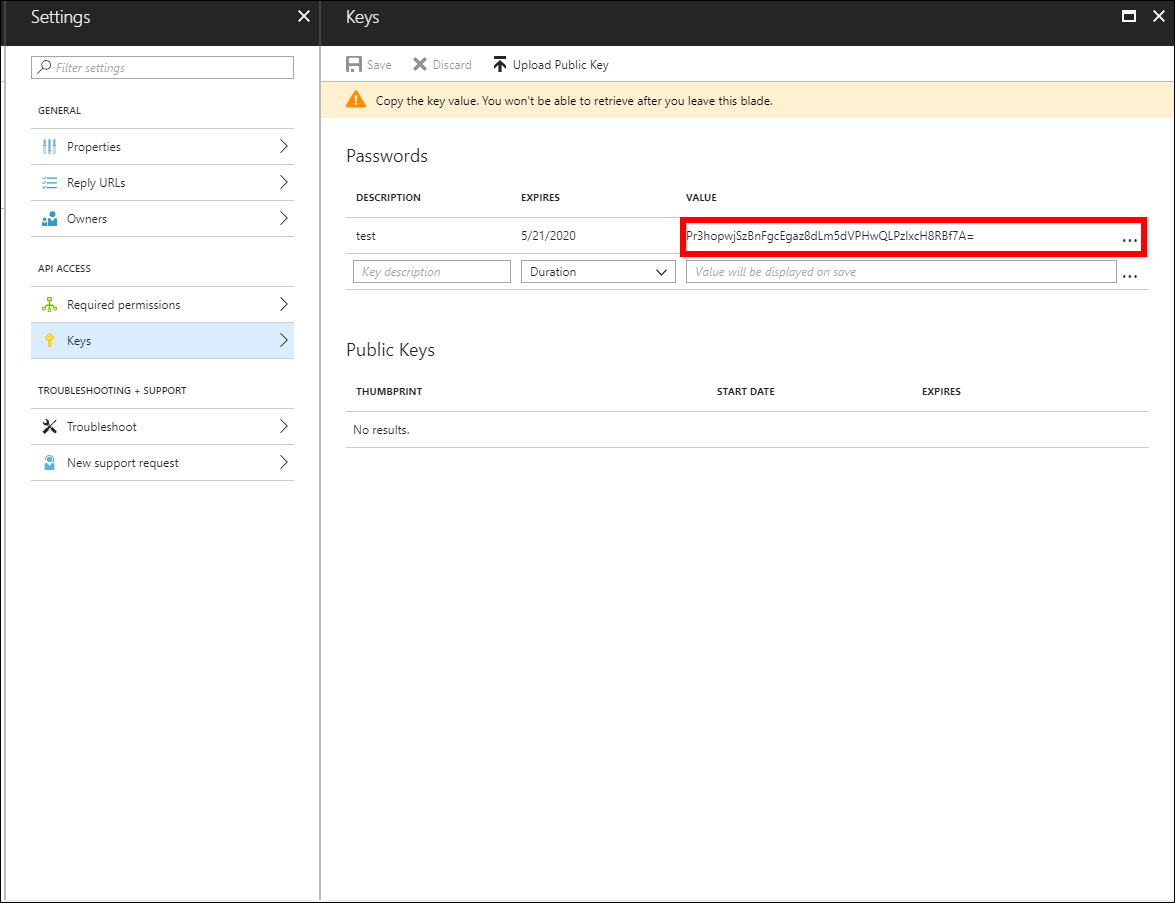
-
Now, test the connection. If the connection is valid, the success message is displayed.
Savethe settings.
The Azure user can be imported into the Syncfusion Report Server. Refer to the following link to Import Azure Active Directory Users and Import Azure Active Directory Groups.
Login with Azure ADFS
After the Single Sign-On settings are saved and the Azure users are imported to the Syncfusion Report Server, you can logout from the application. Now, the login page is provided with the additional button named Microsoft ADFS, which opens the external authentication provider login window, as follows.
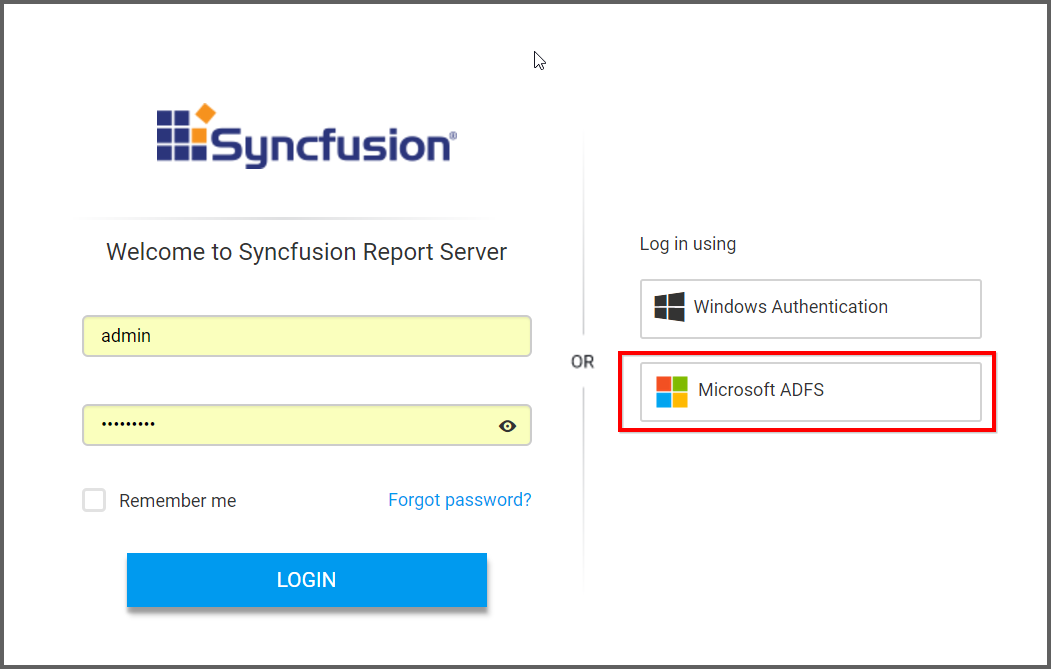
After sign in with the Azure username and password, you can log on to the Syncfusion Report Server.
NOTE
To log on to the Syncfusion Report Server with Azure ADFS, the particular user should be imported to the application. If the user is not imported, it redirects to the login page.